Agile, Secure & Responsive IT Environments
Menu
Menu
Flagship Network’s Security Operations (SecOps) team was working with an electronics parts distributor in Connecticut when it was able to prevent a very costly cyberattack. The SecOps team’s early involvement in securing this distributor’s infrastructure shows how our Flagship Security Framework assists with stopping the cyberattacks from progressing.
This company had a vulnerable Microsoft Exchange server that was exploited by a cybercriminal. This vulnerability was a brand new and unknown to the vendor. The attacker setup a foothold on the server, which is a typical first step required to regain access, if necessary.
They then attempted to setup a cryptocurrency mining operation.
They attempted to move laterally onto other machines within the environment – trying to maximize their profits. They installed Dridex, a sophisticated trojan used to steal banking credentials, onto one of the machines they gained access to.
What were their next steps? It would likely have been to create a ransomware event. Fortunately, the Flagship SecOps team ended the attack before it could fully progress.
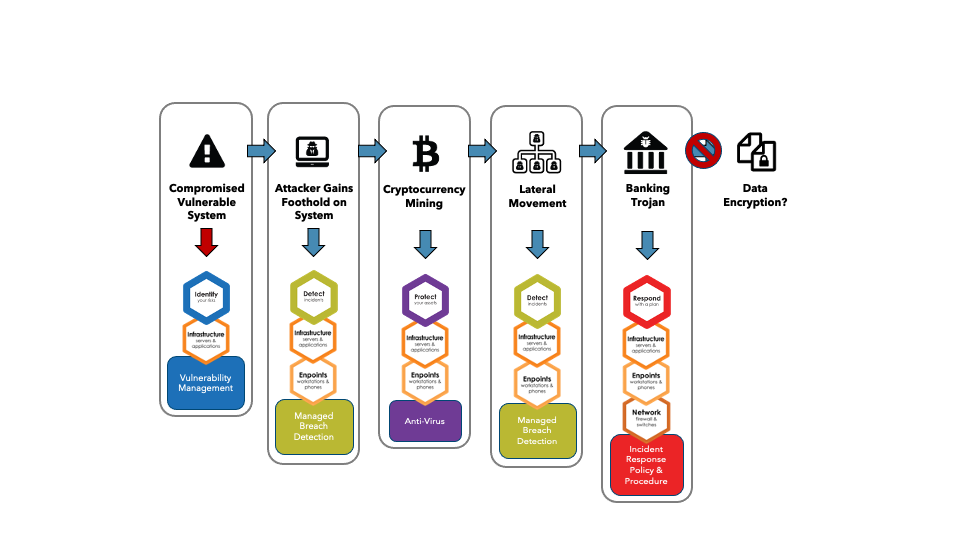
From our framework’s Identify function, infrastructure track and vulnerability management assisted with ensuring all system vulnerabilities are known. In this example, the company did not have vulnerability management software, so the system was left unpatched. Flagship started our involvement of this incident by patching the Exchange server to block any future attempts to exploit.
To help detect incidents on the infrastructure and endpoints, we deployed our Managed Breach Detection service which alerted us of remote web shells active on their Exchange Server. We were able to quickly identify and remove this foothold and cut it off the attacker’s access to the system.
To better Protect the infrastructure and endpoints, we recommended the company install a Sophos managed anti-virus solution, which was able to detect the malicious cryptocurrency mining files and remove them. This allowed us to quickly remediate this phase of the attack.
In the lateral movement phase. Flagship Managed Breach Detection agents alerted us that there was lateral movement within the network. This early indication within this phase is crucial to minimize the overall impact of this attack chain.
And last but certainly not least, utilizing our Incident Response plan, we properly assessed the situation and requested all machines be disconnected from the network (or worst case, powered down). The trojan that was deployed to a single machine, but Dridex is very persistent and if detected, the best course of action is to wipe the machine and rebuilt or restore.
We then assisted with scanning and verifying all machines were clean before allowing them back onto the network. This ensured that the attack chain was stopped in mid-execution and damaged was minimized.
For more information about our Security Framework or to inquire about our complementary security assessments, please complete the form below.
